(77) Microsoft Purview - Endpoint DLP
- Mr B SOE way
- Jun 13, 2023
- 3 min read
Endpoint data loss prevention (Endpoint DLP) extends the activity monitoring and protection capabilities of DLP to sensitive items on Windows 10, Windows 11, and macOS. Activities (like copying to USB devices or printing) performed on sensitive items is visible to users who have access to the activity explorer after devices are onboarded into the Microsoft Purview compliance portal.
Licensing:
Microsoft 365 E5
Microsoft 365 A5 (EDU)
Microsoft 365 E5 compliance
Microsoft 365 A5 compliance
Microsoft 365 E5 information protection and governance
Microsoft 365 A5 information protection and governance
Onboarding:
There is a list of options to onboard devices to Microsoft Defender.
Local script
Group policy
Microsoft Endpoint Configuration Manager
Mobile Device Management/Microsoft Intune
VDI onboarding scripts for non-persistent machines
1. Navigate to https://security.microsoft.com/
2. Scroll down till you see Settings
3. Select Endpoints

4.Scroll down till you see Device Management, select Onboarding. Select the required to onboard your device to Microsoft Defender.

For macOS and other OS's, view here: https://learn.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-getting-started?view=o365-worldwide
Configure Endpoint DLP settings:
Once the devices are onboarded, the next step is to have a look at the Endpoint DLP settings.
1. Navigate to https://compliance.microsoft.com/homepage
2. Select Data loss prevention then select Endpoint DLP settings.

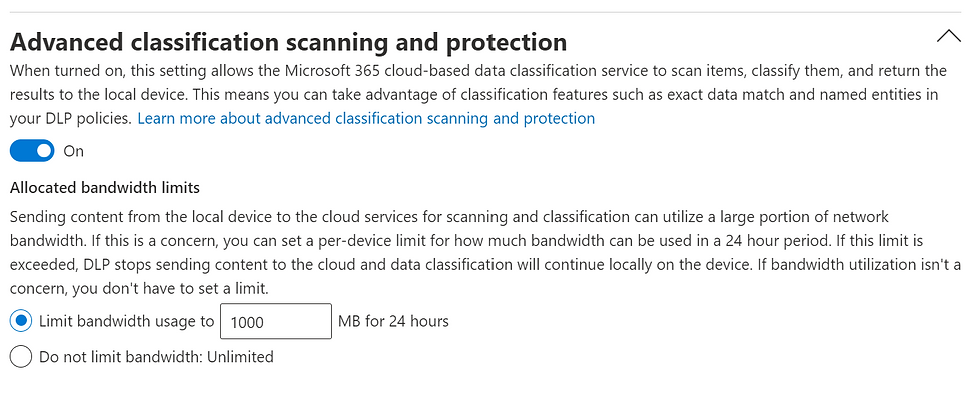
Advanced classification scanning and protection: allows the more advanced Microsoft Purview cloud based data classification service to scan items, classify them and return the results to the local machine.
File path exclusions: To exclude certain paths from DLP monitoring, DLP alerting, and DLP policy enforcement on devices. As certain paths because alerts are too noisy or don’t contain files. Files in those locations aren't audited and any files that are created or modified in those locations aren't subject to DLP policy enforcement.
Restricted apps: A list of applications to configure what actions DLP takes when a user uses an app on the list to access a DLP protected file on a device. It's available for Windows 10 and macOS devices.
Restricted app groups: are collections of apps that are created in DLP settings and then add to a rule in a policy.
Unallowed Bluetooth apps: Prevent people from transferring files protected by policies via specific Bluetooth apps.
Browser and domain restrictions to sensitive data: Restrict sensitive files that match policies from being shared with unrestricted cloud service domains.
Unallowed browsers: For Windows devices, add browsers identified by their executable names that will be blocked from accessing files. These browsers match the conditions of an enforced a DLP policy where the upload to cloud services restriction is set to block or block override. When these browsers are blocked from accessing a file, the end users see a toast notification asking them to open the file through Microsoft Edge. For macOS devices, the full file path must be added.
Service domain restrictions: If all prevented unsupported browsers from accessing sensitive data, it is possible to block supported browsers, like Microsoft Edge, from uploading protected content to specific web services. Service domain restrictions control whether sensitive files protected by your policies are allowed or blocked from accessing specific service domains from Microsoft Edge. Choose Block to prevent certain domains from accessing these files or Allow to specify safe domains. For example, the setting in the image below blocks users from uploading protected content to Dropbox even when using Microsoft Edge. The Service domains setting only applies to files uploaded using Microsoft Edge or Google Chrome with the Microsoft Purview Chrome Extension installed.
Sensitive service domains: When listing a website in Sensitive services domains, this can be audited or blocked with override. Also block users when they attempt to print from a website, copy data from a website, save a website as local files, or upload a sensitive file to an excluded website. This setting is configured in the policy.
3. Under Endpoint DLP Settings, expand on each and configure the following:






Configure DLP Policies:
1. Navigate to https://compliance.microsoft.com/homepage
2. Select Data loss prevention then select policies.
3. Select Create policy.
4. Under locations to apply the policy, untick everything and select "On" for Devices.

5. Under Restrict access or encrypt the content in Microsoft 365 locations section.
Enable the configuration of the Audit or restrict activities on Windows devices section and configure the different activities to Audit, Block or Block with override

6. Select Test or turn on the policy, then select Next then Submit.



Comments