(84) Microsoft Entra - Internet Access
- Mr B SOE way
- Aug 14, 2023
- 4 min read
What is Microsoft Entra Internet Access?
Microsoft Entra Internet access secures your user’s access to Microsoft 365 services and Enterprise applications in your environment while protecting the user’s data from common online threats.
The solution integrates into Microsoft Entra and your user’s identity as a whole across the Microsoft platform to provide seamless and secure access over the internet. It will also help to stop increasingly more common threats such as token replay attacks when combined with the network location check conditions in Conditional Access.
Requirements:
Global Secure Access Administrator role (PIM recommended)
Microsoft Entra ID Premium P1 license (Azure AD Premium P1)
How Microsoft Entra Internet Access works?
Microsoft Entra Internet Access works by deploying a client-side application to the end user’s device to tunnel traffic to the Global Secure Access service, traffic is effectively proxied to the destination services without any impact on performance.
As well as the client-side application, Microsoft Entra Internet Access can also be connected with remote networks by integrating directly with on-premise network routing equipment. This enable connections to be routed directly to the Internet Access service without the need of a client-side application to be deployed. One of the main caveats to this is that Conditional Access policies can only be applied while using the GSA Client and not remote networks.

Instructions:
Step 1: Onboard tenant for remote works:
1. Navigate to onboarding process to onboard tenant.
2. Under "Review tenant information", make sure to review before clicking Next.

3. Under "Send emial to Microsoft", tick "I have sent an email to branchonboarding@microsoft.com" from my work email account. Then select Submit.

It will then display:

Step 2: Create remote work:
To configure remote works,
A Global Secure Access Administrator role in Microsoft Entra ID
Completed the onboarding process for remote networks
The preview requires a Microsoft Entra ID Premium P1 license. If needed, you can purchase licenses or get trial licenses.
To use the Microsoft 365 traffic forwarding profile, a Microsoft 365 E3 license is recommended.
Review the valid configurations for setting up remote networks here - Global Secure Access remote network configurations
1. Navigate to Microsoft Entra, https://entra.microsoft.com with Global Secure Access Administrator.
2. Expand Global Secure Access then expand Devices then select Remote network.
3. Select Create remote network and enter the details

Step 3: Enable and setup traffic forwarding profile
1. Navigate to Microsoft Entra, https://entra.microsoft.com
2. Expand Global Secure Access then Connect
3. Select Activate Global Secure Access in your tenant

4. Allow a few seconds for it to be activated.

5. Under Activate Global Secure Access in your tenant, it will show up as "Tenant onboarding has completed successfully. You can be gin using the product." Select "Get Started".

6. Under Microsoft Entra Internet Access, select "Get started", which re-direct you to the set of instructions.

Step 4: View Microsoft 365 Profile policies & rules
7. From the left hand column, select Traffic forwarding. Tick the box for Microsoft 365 profile, then select Yes.

8. The traffic forwarding traffic is going through the Entra Internet Access proxy service. Now the "Microsoft 365 profile" is enabled.

9. Under "Microsoft 365 traffic policies", select "View" under 3 policies. Expand each policy under Exchange Online, SharePoint Online and OneDrive for Business, and Microsoft 365 Common and Office Online. You will have the options to be enable or disable the rule groups and change the action to forward or bypass for individual rules.

Step 5: Install the Global Secure Access Windows Client
10. There are two options with deploying this to clients:

Option 1: Manually install the client from https://aka.ms/GSAClientDownload
Option 2: Deploy using Microsoft Intune
- Download client from https://aka.ms/GSAClientDownload
- Download Microsoft Win32 Prep Tool from https://github.com/microsoft/Microsoft-Win32-Content-Prep-Tool/blob/master/IntuneWinAppUtil.exe
- Run CMD (Command Prompt) as administrator and CD to Win32 Prep Tool folder
- Run the following to create Intune Win32 App package:
Please specify the source folder: C:\IntuneWin32App\GSAClient
Please specify the setup file: GlobalSecureAccessClient.exe
Please specify the output folder: C:\IntuneWin32App\GSAClient

Once converted, it will look like this

11. Navigate to https://intune.microsoft.com then select Apps then select Windows then select Add then select Windows App (Win32). Upload the recently .intunewin file

12. Under App Information, enter the required details.
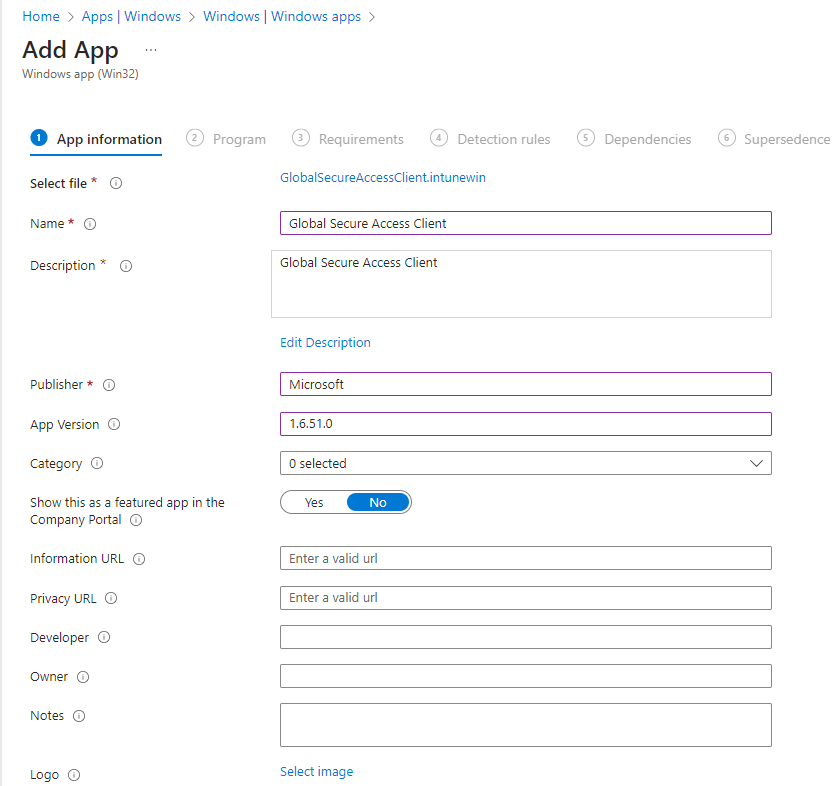
13. Under Programs, enter the following:
Install command: .\GlobalSecureAccessClient.exe /q n
Uninstall command: MsiExec.exe /X{4DB0A026-1C26-4A8C-8378-DCB94900B604} /quiet
Select Next.

14. With Requirements, it is offically supports 64-bit and a minimum operating system. Under Detection rules, enter the following:
Rule type: File
Path: C:\Program Files\Global Secure Access Client
File or folder: GlobalSecureAccessTunnelingService.exe
Detection method: File or folder exists
Associated with a 32-bit app on 64-bit clients: No

Dependencies and supersedence rules can be ignored. Then assign to all devices.
Step 6: Enable Global Secure Access signalling
What is Global Secure Access Signalling?
Global Secure Access signalling is an important feature as without it, source IP information will not be accurate in the Microsoft Entra ID audit logs. This can have adverse effects in the accuracy of reporting and more importantly, any Conditional Access policies which enforce access based on trusted locations.
15. Navigate to https://entra.microsoft.com/ then expand Global Secure Access then expand Global settings then select Session management. Then select Adaptive Access then tick the box to "Enable Global Secure Access signalling in Conditional Access".

16. Select Save.

Step 7: Configure Conditional Access Policies
Conditional Access can be used alongside the Global Secure Access client to ensure that only compliance devices can authenticate and connect to the client. Creating multiple policies that target both the client and location will enable you to create a secure access solution for your Microsoft 365 services and applications.
17. Create two Conditional Access policies with the following:
Policy 1:
This policy will target Exchange Online, SharePoint Online and any cloud apps as required. Currently, only these services are supported by the Microsoft 365 traffic profile, so eventually this policy can be expanded to cover all cloud apps. The policy will target all locations with an exclusion ‘All Compliant Network locations’. The policy will be set to block.
Name: Location Block Baseline
Target Resources: Exchange Online & SharePoint Online
Conditions: Include: Any location, Exclude: All Compliance Network locations
Grant: Block Access
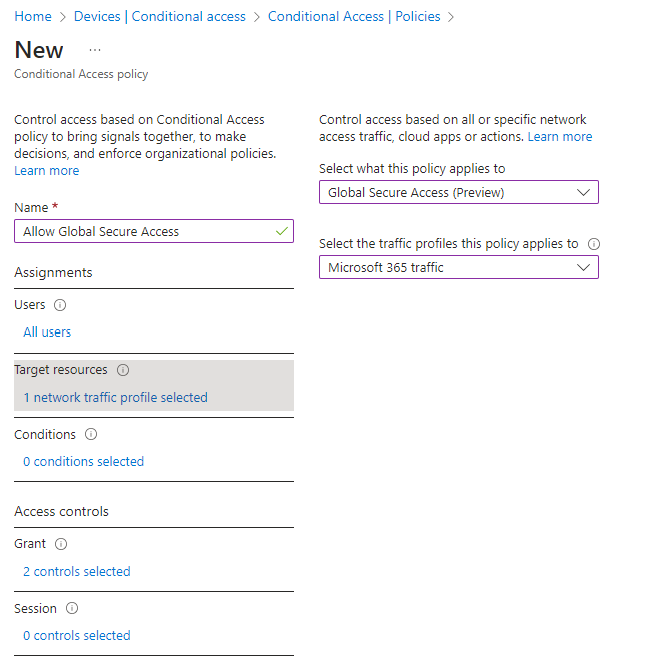
Policy 2:
This policy will target the Global Secure Access resource with the Microsoft 365 traffic policy applied and it will include a grant control for requiring MFA and a compliant device.
Name: Allow Global Secure Access
Users: All Users
Target resources: Global Secure Access: Microsoft 365 traffic
Grant: Require MFA & Compliance device



Comments