(85) Microsoft Entra - Protection - Identity Secure Score
- Mr B SOE way
- Aug 14, 2023
- 2 min read
What is Identity Secure Score?
Identity Secure Score provides organisations with increased visibility and control over their security posture by discovering opportunities that will help to improve security across the organisation. These opportunities are surfaced as recommendations, which are coupled with the guidance and the workflows necessary to help security administrators implement each recommendation. The more improvements made, the more the identity security posture improves—increasing your identity secure score.
How to access Identity Secure Score?
To access Identity Secure Score, navigate to here.
Overall my personal tenant is at 74.39%, by viewing the "Status" with To address needs to be uplifted.

Improvement Actions:
Policy 1: Protect all users with a user risk policy:
Against each improvement actions, by clicking on each policy it will provide a "Improvement action" with a set of instructions. In this case for "Protect all users with a user risk policy", create a Conditional Access policy either manual or create a template.

By navigating to here for Conditional Access Policies, select New policy from template under Zero Trust. Ensure to set policy as "Report-only".

By viewing the Conditional Access Policy, you will see that "User risk" is set to High.

Navigate here to configure User risk policy which by default is set with the following.

Configure the user risk to High, select Done then select Policy enforcement as Enabled.
Enable policy to block legacy authentication

Policy 2: Enable policy to block legacy authentication:
Select the policy, the improvment action will show up. Select Microsoft 365 MFA wizard. This will load to this page. Depending on the environment setup, other options are available.

Alternatively, create a Conditional Access policy to block legacy authentication under Secure Foundation.

Policy 3: Do not allow users to grant consent to unreliable applications:
Navigate to https://portal.azure.com/ then select Enterprise applications then select Consent and permissions. Then select "Allow user consent from apps from verified publishers, for selected permissions (Recommended)"
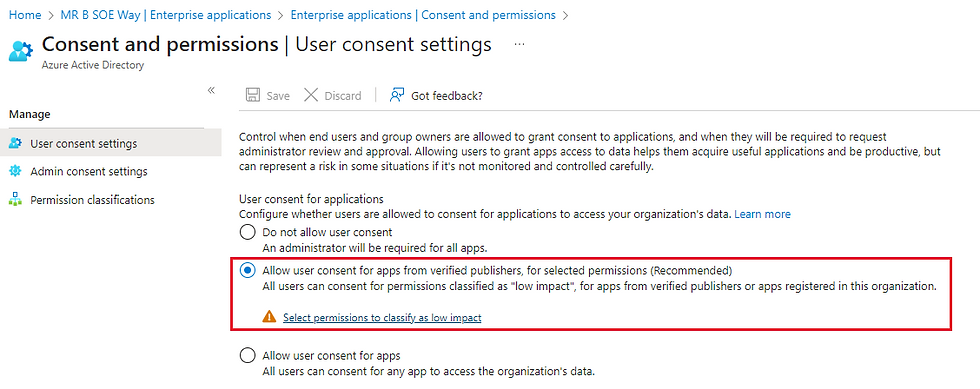
It is optional to click on "select permissions to classify as low impact" which will load the page to "Permission classifications". Optionally to help users to consent to apps that require admin consent workflow, it is recommended to use Admin consent settings. Make the required changes and select Save.

Policy 4: Set a honeytoken account:
An overview of a honeytoken is setting honeytoken accounts helps to trap malicious actors. Any authentication attempt associated with these accounts (normally dormant) will trigger a Defender for Identity security alert and will improve your chances to detect advanced threats.
Navigate to https://security.microsoft.com/settings/identities then under Entity tags then select Honeytoken. Select a user from the list.

Any changes made will be reflected in Identity Secure Score in the next 48 hours.



Comments