(86) Defender for Endpoint - Onboarding
- Mr B SOE way
- Aug 15, 2023
- 3 min read
Microsoft Defender for Endpoint (MDE) is part of the Microsoft Defender platform, and is designed to protect devices and endpoints from various cyber threats. To implement this product successfully, the first step is ensuring efficient onboarding of new devices.
What licenses are required for Microsoft Defender for Endpoint?

What are the supported Windows versions?
Windows 11 Enterprise
Windows 11 Education
Windows 11 Pro
Windows 11 Pro Education
Windows 10 Enterprise
Windows 10 Enterprise LTSC 2016 (or later)
Windows 10 Enterprise IoT*
Windows 10 Education
Windows 10 Pro
Windows 10 Pro Education
Windows 8.1 Enterprise**
Windows 8.1 Pro**
Windows 7 SP1 Enterprise**
Windows 7 SP1 Pro**
Windows server
Windows Server 2008 R2 SP1**
Windows Server 2012 R2
Windows Server 2016
Windows Server, version 1803 or later
Windows Server 2019 and later
Windows Server 2019 core edition
Windows Server 2022
Windows Server 2022 core edition
Azure Virtual Desktop
Windows 365 running one of the above operating systems/versions
What are the other supported operating systems?
macOS
Linux
Android
iOS
Option 1: Microsoft Intune
If you are already using Microsoft Intune for managing devices, onboarding the devices in Microsoft Defender for Endpoint through Intune will automatically become the most logical and efficient method. This method involves pushing apps or configuration profiles to the devices, a task familiar to most Intune administrators.
For Windows devices, the Microsoft Defender app is already built-in to the operating system. So you will only need to enable and configure the Microsoft Defender for Endpoint sensor, which is available as a Windows service called Windows Defender Advanced Threat Protection Service, or MsSense.exe.
To create the configuration profile, navigate to Endpoint Security and create an Endpoint Detection and Response policy.

For macOS, you will need to follow this guide.
For iOS, you will need to setup and deploy Microsoft Defender (VPP) using the Apple Business Manager or Apple School Manager.
For Android, you will need to setup managed google play store, and deploy Defender for Endpoint on Android.
Option 2: Onboarding packages and scripts
Not all companies are ready to have their devices managed by Microsoft Intune. Some may use a different management platform, and others have a certain number of devices that are not being or cannot be managed for various reasons. When in this situation, deploying a script or onboarding package with any deployment tool is the way to go.
Get started by directly downloading the necessary scripts and packages from the Microsoft Defender admin center.

Alternatively if your tenant does not have a license for MDE, you can always onboard to another tenant by downloading the "Local script" then running Command Prompt as administrator then running the cmd file.
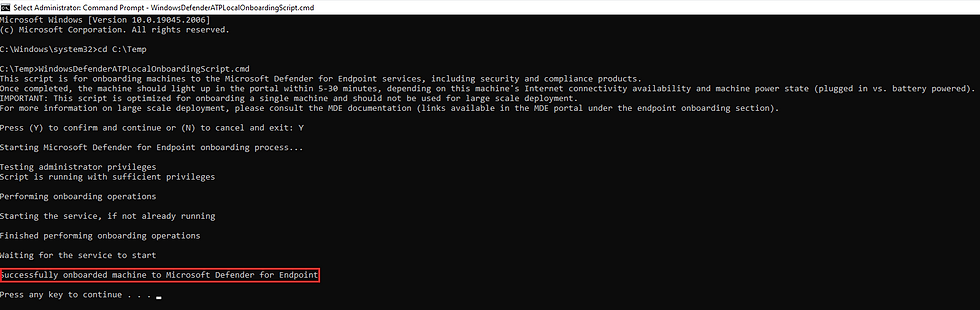
Where in this instance, I ran this script my VM that is connected MR B SOE Way, as I don't have a license. It is onboarded to my work's dev tenant where it shows it has been onboarded.

Most of these scripts or packages can be easily deployed on the endpoints, except for the VDI scripts used with non-persistent devices. These scripts require you to onboard a new device every time a new user signs in, which can create some challenges.
Option 3: Device Discovery
Microsoft Defender for Endpoint’s Device Discovery feature allows us to actively scan the corporate network for any unmanaged devices that have not been onboarded yet. This is a valuable tool as it provides visibility and protection for devices that were previously invisible. To enable this feature, navigate to the Settings > Endpoints section in the Microsoft Defender admin portal.

Once enabled and configured, device discovery will use already onboarded devices to scan for new devices. As new devices are discovered, they’ll appear in the inventory, ready for onboarding.
Option 4: Personal Devices
Not all devices used by employees are corporate-owned; some companies allow their employees to work from personal devices too. When dealing with this situation, deploying the app conventionally isn’t an option as employees prefer not to have their personal devices managed by the company.
Instead, we can enforce the installation of Microsoft Defender for Endpoint when they access corporate data. This involves implementing Mobile Application Management (MAM) and configuring the “Max allowed device threat level” setting in the “Conditional launch” page of the app protection policy.

Additionally, activate the app protection policy evaluation for Android & iOS devices in the Microsoft Defender for Endpoint connector settings. This ensures that the app protection policy is allowed to asses device’s threat health.

After configuration, Microsoft will prompt users to install the MDE app before allowing access to corporate data.
For personal Windows devices, a similar solution is available through Microsoft’s recent release of MAM for Windows in Public Preview



Comments